Overview
Install and Configure Root CA
First need to temporarily add your account as member of “Enterprise Admins”
Add-ADGroupMember -Identity "Enterprise Admins" -Members $([System.Security.Principal.WindowsIdentity]::GetCurrent().User.Value)Add AD-CS Role and management tools
$LAB_Internal_Root = @{
CAType = 'EnterpriseRootCA'
ValidityPeriod = 'Years'
ValidityPeriodUnits = 2
CACommonName = "LAB Internal Root"
CryptoProviderName = "RSA#Microsoft Software Key Storage Provider"
KeyLength = 4096
HashAlgorithmName = 'SHA256'
DatabaseDirectory = "$($env:SystemRoot)\system32\CertLog"
LogDirectory = "$($env:SystemRoot)\system32\CertLog"
}
Install-AdcsCertificationAuthority @LAB_Internal_Root -Confirm:$false
Install and Configure Issuing CA
First make sure the newly created Root CA certificate has been added to the local machine trusted root certificate store on the domain joined computer and remove any installed
Get-ChildItem Cert:\LocalMachine\Root | ?{$_.DnsNameList -eq "LAB Internal Root"}
Get-ChildItem Cert:\LocalMachine\My | Remove-Item
Add and configure AD-CS Role
$LAB_Internal_Subordinate = @{
CAType = 'EnterpriseSubordinateCA'
ValidityPeriod = 'Years'
ValidityPeriodUnits = 1
CACommonName = "LAB Internal Issuing CA"
CryptoProviderName = "RSA#Microsoft Software Key Storage Provider"
KeyLength = 2048
HashAlgorithmName = 'SHA256'
DatabaseDirectory = "$($env:SystemRoot)\system32\CertLog"
LogDirectory = "$($env:SystemRoot)\system32\CertLog"
ParentCA = "LABCSROOT.lab.intrasolve.com\LAB Internal Root"
}
Install-AdcsCertificationAuthority @LAB_Internal_Subordinate -Confirm:$false
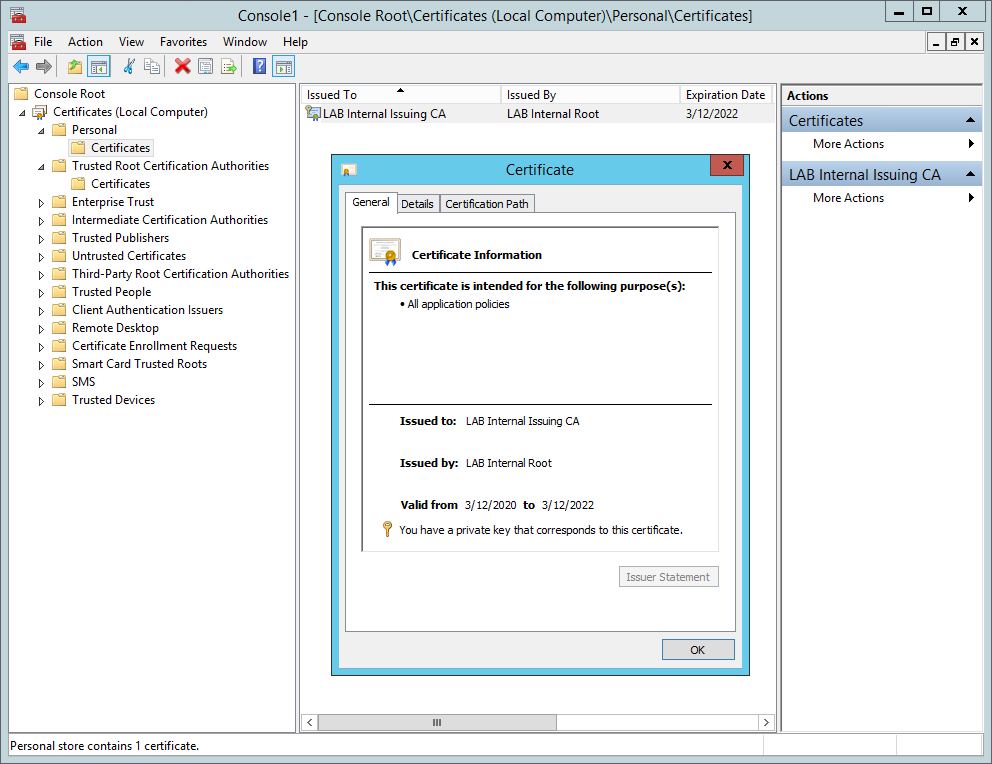
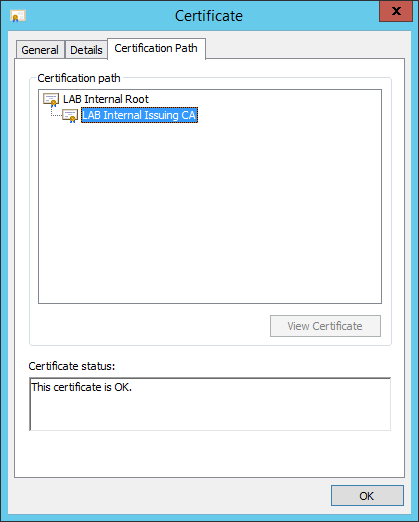
You should now see the subordinate certificate installed with private key and chaining up to root CA
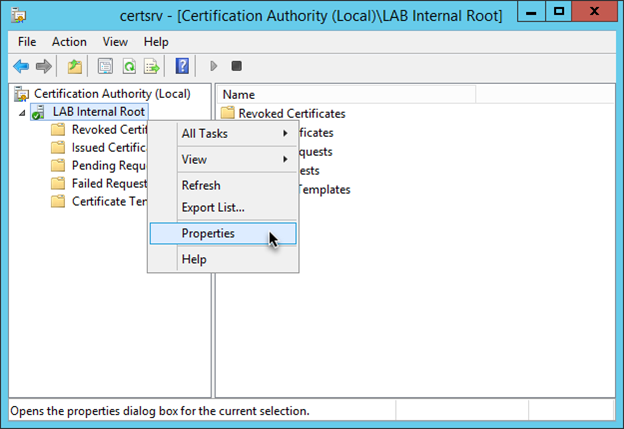
Configure CRD and AIA Extensions (manual steps)
From Root CA: Certification Authority > Properties > Extensions tab
Select CRL Distribution Point (CDP)
Remove last 2
Add location:
http://LABCSISSUE.lab.intrasolve.com\CertEnroll\<ServerDNSName>_<CaName><CertificateName>.crt
Select Authority Information Access (AIA)
Now go ahead and disable the NIC on the Root CA (logon to console thru vSphere)
Disable-NetAdapter eth0 -Confirm:$falseConfigure AD-DS Domain Controllers
Create template
# Import PKI module
Import-Module '.\PSPKI'
Cleanup needed on Domain Controllers
# Force check for new CA cert
Remove-Item HKLM:\SOFTWARE\Microsoft\Cryptography\AutoEnrollment\AEDirectoryCache -Recurse -Confirm:$false
Enroll from newly created template